Industry News
Jan 28, 2025
Industry News
Industry News



Photo by: Reuters
FBI uncovered how North Korean hackers stole hundreds of millions in Bitcoin from a Japanese crypto exchange.
The exchange, DMM Bitcoin, decided to shut down after the incident and plans to refund affected users.
North Korean hackers stole $1.3 billion from the crypto industry in 2024.
The U.S. Federal Bureau of Investigation (FBI) and its international partners recently exposed how North Korean cyber actors stole hundreds of millions from the now-defunct Japanese crypto exchange DMM Bitcoin.
DMM Bitcoin announced its plan to shut down on December 2, nearly seven months after it suffered one of the biggest hacks in crypto history. On May 31, hackers siphoned off 4,502.9 BTC ($308 million) from the exchange following what it termed an “unauthorized leak of Bitcoin” from its wallet. The trading platform paused withdrawals the same day before touting a recovery plan to refund users on June 5.
According to a recent statement, the FBI, Department of Defense Cyber Crime Center (DC3), and National Police Agency (NPA) of Japan linked the $308 million Bitcoin heist to North Korean hackers, whom they claimed used TraderTraitor threat activity.
Also tracked as Jade Sleet, UNC4899, and Slow Pisces, TraderTraitor activity includes a series of malicious applications written using cross-platform JavaScript code with the Node.js runtime environment using the Electron framework, often disguised as crypto trading or price prediction tools. TraderTraitor is commonly associated with targeted social engineering attacks directed at multiple employees of the same cryptocurrency company simultaneously.
“Intrusions begin with a large number of spearphishing messages sent to employees of cryptocurrency companies—often working in system administration or software development/IT operations (DevOps)—on a variety of communication platforms. The messages often mimic a recruitment effort and offer high-paying jobs to entice the recipients to download malware-laced cryptocurrency applications.” The FBI explained in a separate report.
The FBI noted that a North Korean cyber actor using TraderTraitor activity masqueraded as a recruiter on LinkedIn before contacting an employee at Ginco, a Japan-based enterprise cryptocurrency wallet software company, in late March.
The victim, who maintained access to Ginco’s wallet management system, was compromised around the same time when the hacker duped them into clicking a malicious URL disguised as a pre-employment test located on a GitHub page.
Per the statement, the breach allowed the actor to exploit session cookie information and impersonate the compromised employee to gain access to Ginco’s communication systems, which authorities believe were unencrypted.
“In late-May 2024, the actors likely used this access to manipulate a legitimate transaction request by a DMM employee, resulting in the loss of 4,502.9 BTC, worth $308 million at the time of the attack,” the statement read, noting that the stolen funds were shifted to TraderTraitor-controlled wallets.
The FBI’s statement followed a Chainalysis report that highlighted how North Korean actors were responsible for over half of crypto thefts in 2024.
According to the report, North Korean actors stole $1.34 billion in crypto across 47 incidents in 2024, accounting for 61% of the $2.2 billion in digital assets stolen this year and 20% of total incidents. This figure also represented a 102.88% increase in value stolen by the DPRK-affiliated hackers, who were responsible for the theft of $660.50 million across 20 incidents in 2023.
Chainalysis noted that compared to other hacks observed, North Korean actors had been consistently responsible over the last three years for most “large-sized” attacks, with exploits involving between $50 and $100 million, and those above $100 million occurring more frequently this year than they did in 2023.
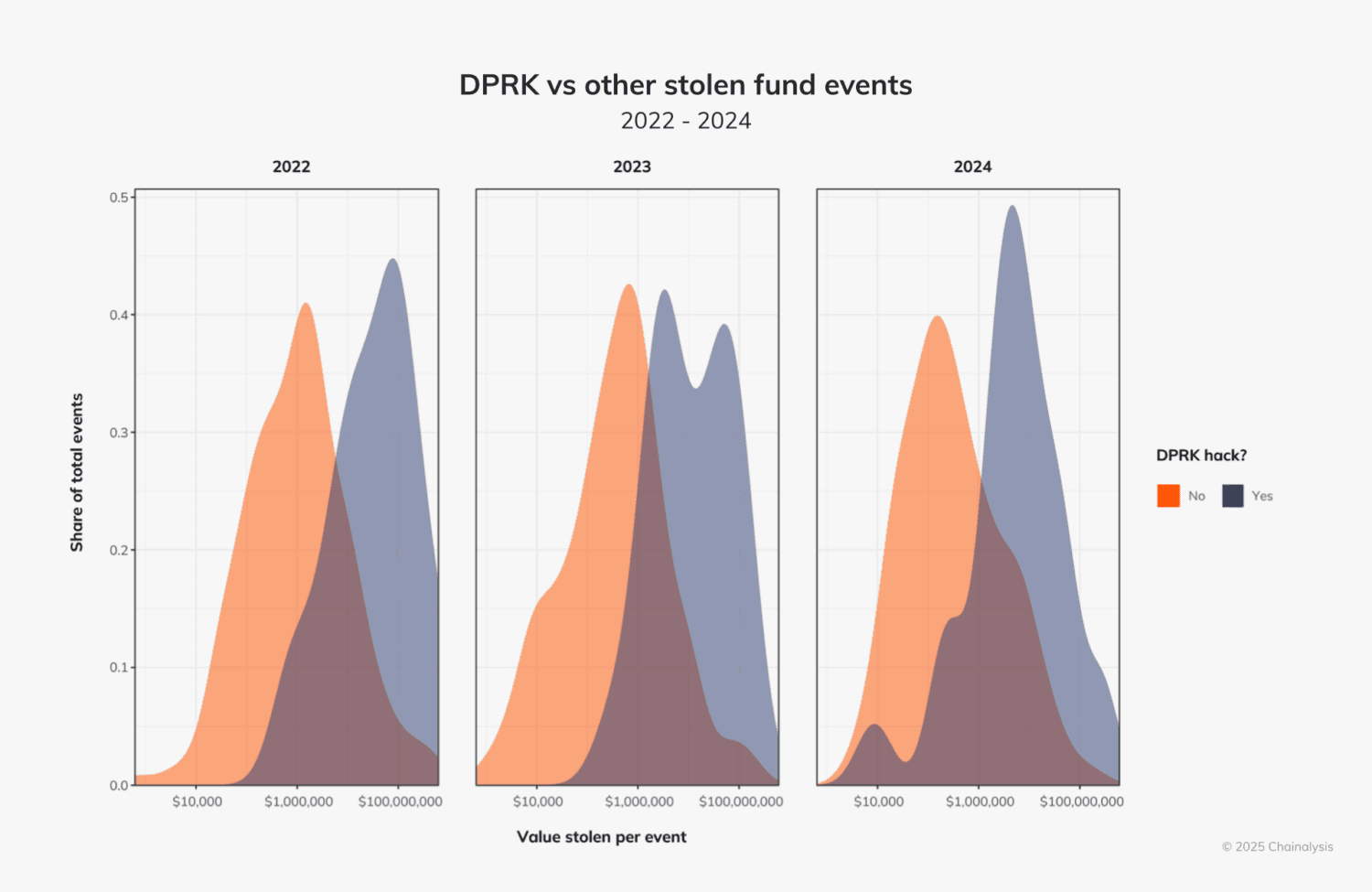
Chart by Chainalysis
The report linked some of these incidents to DPRK IT workers using sophisticated Tactics, Techniques, and Procedures (TTPs), such as false identities, dubious remote work opportunities, and third-party hiring intermediaries to infiltrate and compromise crypto or Web3 companies.
Regarding the DMM Bitcoin hacking incident, Chainalysis said North Korean actors moved the stolen funds to multiple intermediary addresses before ultimately sending the entire loot to a Bitcoin CoinJoin Mixing Service.
After mixing the stolen funds, the attackers transferred some of the assorted digital assets to several bridging services and later to Huione Guarantee, an online marketplace linked to Cambodian conglomerate Huione Group, which was previously named a significant placer in cybercrimes.
While the devastating May hack drove DMM Bitcoin out of business, the exchange fully covered customer deposits by seeking equivalent funds with the backing of group companies. The exchange confirmed in December that it would transfer accounts and assets to the trading platform SBI VC Trade in March, 2025.
FBI uncovered how North Korean hackers stole hundreds of millions in Bitcoin from a Japanese crypto exchange.
The exchange, DMM Bitcoin, decided to shut down after the incident and plans to refund affected users.
North Korean hackers stole $1.3 billion from the crypto industry in 2024.
The U.S. Federal Bureau of Investigation (FBI) and its international partners recently exposed how North Korean cyber actors stole hundreds of millions from the now-defunct Japanese crypto exchange DMM Bitcoin.
DMM Bitcoin announced its plan to shut down on December 2, nearly seven months after it suffered one of the biggest hacks in crypto history. On May 31, hackers siphoned off 4,502.9 BTC ($308 million) from the exchange following what it termed an “unauthorized leak of Bitcoin” from its wallet. The trading platform paused withdrawals the same day before touting a recovery plan to refund users on June 5.
According to a recent statement, the FBI, Department of Defense Cyber Crime Center (DC3), and National Police Agency (NPA) of Japan linked the $308 million Bitcoin heist to North Korean hackers, whom they claimed used TraderTraitor threat activity.
Also tracked as Jade Sleet, UNC4899, and Slow Pisces, TraderTraitor activity includes a series of malicious applications written using cross-platform JavaScript code with the Node.js runtime environment using the Electron framework, often disguised as crypto trading or price prediction tools. TraderTraitor is commonly associated with targeted social engineering attacks directed at multiple employees of the same cryptocurrency company simultaneously.
“Intrusions begin with a large number of spearphishing messages sent to employees of cryptocurrency companies—often working in system administration or software development/IT operations (DevOps)—on a variety of communication platforms. The messages often mimic a recruitment effort and offer high-paying jobs to entice the recipients to download malware-laced cryptocurrency applications.” The FBI explained in a separate report.
The FBI noted that a North Korean cyber actor using TraderTraitor activity masqueraded as a recruiter on LinkedIn before contacting an employee at Ginco, a Japan-based enterprise cryptocurrency wallet software company, in late March.
The victim, who maintained access to Ginco’s wallet management system, was compromised around the same time when the hacker duped them into clicking a malicious URL disguised as a pre-employment test located on a GitHub page.
Per the statement, the breach allowed the actor to exploit session cookie information and impersonate the compromised employee to gain access to Ginco’s communication systems, which authorities believe were unencrypted.
“In late-May 2024, the actors likely used this access to manipulate a legitimate transaction request by a DMM employee, resulting in the loss of 4,502.9 BTC, worth $308 million at the time of the attack,” the statement read, noting that the stolen funds were shifted to TraderTraitor-controlled wallets.
The FBI’s statement followed a Chainalysis report that highlighted how North Korean actors were responsible for over half of crypto thefts in 2024.
According to the report, North Korean actors stole $1.34 billion in crypto across 47 incidents in 2024, accounting for 61% of the $2.2 billion in digital assets stolen this year and 20% of total incidents. This figure also represented a 102.88% increase in value stolen by the DPRK-affiliated hackers, who were responsible for the theft of $660.50 million across 20 incidents in 2023.
Chainalysis noted that compared to other hacks observed, North Korean actors had been consistently responsible over the last three years for most “large-sized” attacks, with exploits involving between $50 and $100 million, and those above $100 million occurring more frequently this year than they did in 2023.

Chart by Chainalysis
The report linked some of these incidents to DPRK IT workers using sophisticated Tactics, Techniques, and Procedures (TTPs), such as false identities, dubious remote work opportunities, and third-party hiring intermediaries to infiltrate and compromise crypto or Web3 companies.
Regarding the DMM Bitcoin hacking incident, Chainalysis said North Korean actors moved the stolen funds to multiple intermediary addresses before ultimately sending the entire loot to a Bitcoin CoinJoin Mixing Service.
After mixing the stolen funds, the attackers transferred some of the assorted digital assets to several bridging services and later to Huione Guarantee, an online marketplace linked to Cambodian conglomerate Huione Group, which was previously named a significant placer in cybercrimes.
While the devastating May hack drove DMM Bitcoin out of business, the exchange fully covered customer deposits by seeking equivalent funds with the backing of group companies. The exchange confirmed in December that it would transfer accounts and assets to the trading platform SBI VC Trade in March, 2025.
FBI uncovered how North Korean hackers stole hundreds of millions in Bitcoin from a Japanese crypto exchange.
The exchange, DMM Bitcoin, decided to shut down after the incident and plans to refund affected users.
North Korean hackers stole $1.3 billion from the crypto industry in 2024.
The U.S. Federal Bureau of Investigation (FBI) and its international partners recently exposed how North Korean cyber actors stole hundreds of millions from the now-defunct Japanese crypto exchange DMM Bitcoin.
DMM Bitcoin announced its plan to shut down on December 2, nearly seven months after it suffered one of the biggest hacks in crypto history. On May 31, hackers siphoned off 4,502.9 BTC ($308 million) from the exchange following what it termed an “unauthorized leak of Bitcoin” from its wallet. The trading platform paused withdrawals the same day before touting a recovery plan to refund users on June 5.
According to a recent statement, the FBI, Department of Defense Cyber Crime Center (DC3), and National Police Agency (NPA) of Japan linked the $308 million Bitcoin heist to North Korean hackers, whom they claimed used TraderTraitor threat activity.
Also tracked as Jade Sleet, UNC4899, and Slow Pisces, TraderTraitor activity includes a series of malicious applications written using cross-platform JavaScript code with the Node.js runtime environment using the Electron framework, often disguised as crypto trading or price prediction tools. TraderTraitor is commonly associated with targeted social engineering attacks directed at multiple employees of the same cryptocurrency company simultaneously.
“Intrusions begin with a large number of spearphishing messages sent to employees of cryptocurrency companies—often working in system administration or software development/IT operations (DevOps)—on a variety of communication platforms. The messages often mimic a recruitment effort and offer high-paying jobs to entice the recipients to download malware-laced cryptocurrency applications.” The FBI explained in a separate report.
The FBI noted that a North Korean cyber actor using TraderTraitor activity masqueraded as a recruiter on LinkedIn before contacting an employee at Ginco, a Japan-based enterprise cryptocurrency wallet software company, in late March.
The victim, who maintained access to Ginco’s wallet management system, was compromised around the same time when the hacker duped them into clicking a malicious URL disguised as a pre-employment test located on a GitHub page.
Per the statement, the breach allowed the actor to exploit session cookie information and impersonate the compromised employee to gain access to Ginco’s communication systems, which authorities believe were unencrypted.
“In late-May 2024, the actors likely used this access to manipulate a legitimate transaction request by a DMM employee, resulting in the loss of 4,502.9 BTC, worth $308 million at the time of the attack,” the statement read, noting that the stolen funds were shifted to TraderTraitor-controlled wallets.
The FBI’s statement followed a Chainalysis report that highlighted how North Korean actors were responsible for over half of crypto thefts in 2024.
According to the report, North Korean actors stole $1.34 billion in crypto across 47 incidents in 2024, accounting for 61% of the $2.2 billion in digital assets stolen this year and 20% of total incidents. This figure also represented a 102.88% increase in value stolen by the DPRK-affiliated hackers, who were responsible for the theft of $660.50 million across 20 incidents in 2023.
Chainalysis noted that compared to other hacks observed, North Korean actors had been consistently responsible over the last three years for most “large-sized” attacks, with exploits involving between $50 and $100 million, and those above $100 million occurring more frequently this year than they did in 2023.

Chart by Chainalysis
The report linked some of these incidents to DPRK IT workers using sophisticated Tactics, Techniques, and Procedures (TTPs), such as false identities, dubious remote work opportunities, and third-party hiring intermediaries to infiltrate and compromise crypto or Web3 companies.
Regarding the DMM Bitcoin hacking incident, Chainalysis said North Korean actors moved the stolen funds to multiple intermediary addresses before ultimately sending the entire loot to a Bitcoin CoinJoin Mixing Service.
After mixing the stolen funds, the attackers transferred some of the assorted digital assets to several bridging services and later to Huione Guarantee, an online marketplace linked to Cambodian conglomerate Huione Group, which was previously named a significant placer in cybercrimes.
While the devastating May hack drove DMM Bitcoin out of business, the exchange fully covered customer deposits by seeking equivalent funds with the backing of group companies. The exchange confirmed in December that it would transfer accounts and assets to the trading platform SBI VC Trade in March, 2025.
Share this article
Related Articles
Related Articles
Related Articles