Blockchain Technology
Jan 10, 2025
Blockchain Technology
Blockchain Technology



Blockchain technology has fundamentally transformed trustless transactions by creating an ecosystem where total strangers can transact with one another without the need for an intermediary. At the heart of this revolution lies cryptography, the science of encoding and decoding information. Blockchain networks use cryptography in several different ways to make sure only honest and legitimate transactions can go through the network and filter out any malicious activity.
Most people know about cryptocurrency and many own and use it. But only a few know about how cryptocurrencies work. In this article, let’s explore the role that cryptography plays in maintaining a blockchain and understand where the ‘crypto’ in cryptocurrency comes from.
Cryptography is the science of securing communication and information by encoding it on one end and decoding it on the other end. This process ensures that the communication can only be read by the intended recipient and no one else. In general, blockchain cryptography uses two different types of encryptions to encrypt data and achieve the process of encoding and decoding information.
Secret key cryptography, also known as symmetric key cryptography, is a process through which a single key is used to encrypt and decrypt the data on both ends. While simple to execute, this process creates a security risk, especially in large networks. Since the encryption and decryption keys are the same, anyone who manages to get the encryption key will also be able to decrypt the message, making it more susceptible to malicious attacks.
Also known as asymmetric key cryptography, this is a process through which a pair of related keys, one public and one private, is used to encrypt and decrypt the data. It can be used to convert plaintext into encrypted data using private keys to ensure the integrity and authenticity of the transaction data.
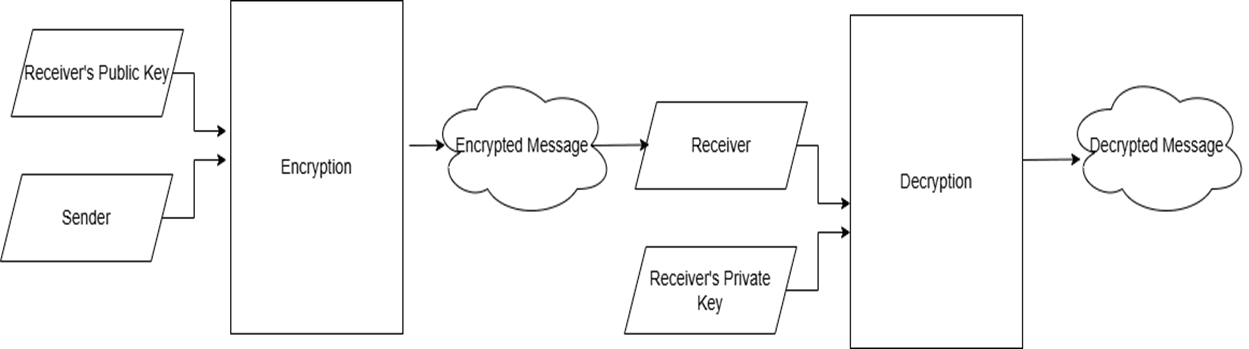
The public key of a network participant is available to everyone. Therefore, anyone can use it to encrypt a message to that particular person. This process is called ‘Public Key Encryption’ and it’s used to encrypt messages on an open network that can only be read by the intended recipient.
The private key is only available to the participant and therefore only they can use it to decrypt the message. The exact steps of asymmetric encryption are as follows:
The sender uses the receiver’s public key to encrypt the information.
Sender sends the encrypted information to the receiver.
Receiver uses the private key to carry out the decryption process and reveal the information.
All blockchains use cryptography extensively to secure their network. From making transactions to maintaining the integrity of the data on the blocks, cryptography forms the basis upon which most blockchain security. Let’s look at some of those use cases in detail:
The Asymmetric encryption method described above is used to make secure transactions on the blockchain. For example, on the Bitcoin network, when users send Bitcoin to others, they use the public key of the receiving user to encrypt that transaction. The transaction is then recorded on the blockchain and only the user who holds the private key can then decrypt that transaction and get access to the Bitcoin. This process secures the Bitcoins on the network, despite the network’s data being open to the public and the network itself being decentralized.
Cryptographic hashing is a mathematical function and a cryptographic algorithm that takes any input value and produces a fixed-size output known as a Hash. This function is used to create a cryptographic hash for each block in a blockchain that represents all the data within that particular block. If any miner or validator were to change the data stored on the blockchain ledger even slightly, the hash algorithm will produce a different hash value which will not match with the hash of other validators. This process makes it easy to detect malicious activity on the blockchain and secures data and networks integrity. It also makes sure the data on a blockchain is recorded securely, enhancing blockchain security.
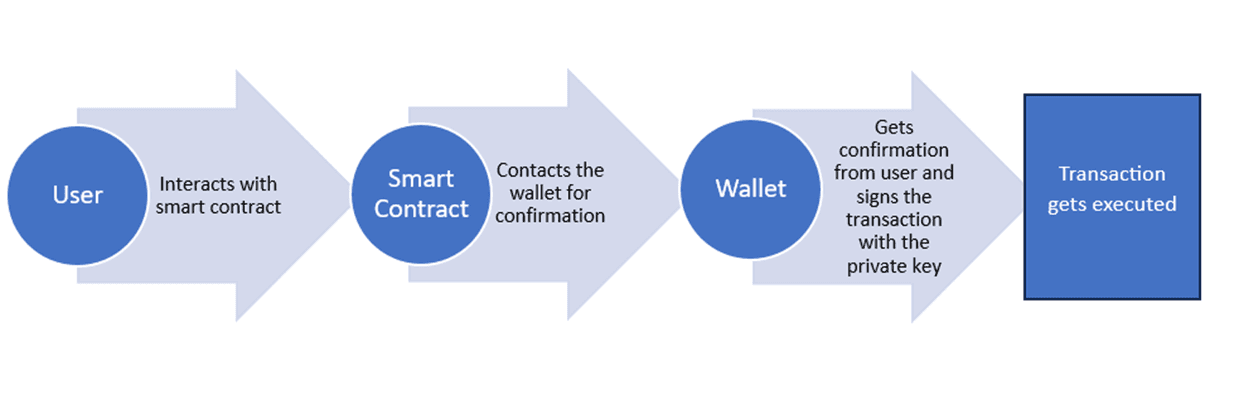
Blockchain transactions are authenticated with digital signatures that are secured by cryptography. When a web3 user interacts with any smart contract and carries out a transaction, that transaction is authenticated by a private key, also known as secret key, that's stored in the wallet. This private key allows the blockchain network to verify that the person making the transaction is the owner of that account. It’s this process that also gives rise to the crypto maxim ‘Not your key, not your coin’. Because as far as the network is concerned, the person who owns the private key is the owner of the account.
Proof of Work blockchains like Bitcoin also rely on complex mathematical challenges based on cryptographic hash functions to validate new blocks. Miners compete to solve these puzzles and the first one to do so earns the right to add the next block to the blockchain. This process often requires significant computational resources which ensures that miners incur real costs to participate in the network. As a reward for their efforts, miners receive a specific amount of newly minted Bitcoin, this aligns the financial incentive of the miners with the security of the underlying blockchain ledger.
Adding cryptographic techniques like Zero-Knowledge proof can be used to protect user identity and transaction details. Zero Knowledge Proof allows one party to prove to another that a specific condition has been met without revealing any associated information. Such methods are used by privacy-focused blockchains like Zcash. It allows users to create transactions that does not reveal transaction data like the sender address, receiver’s address, and the amount of coins sent to the wider public. Using this method creates a fully public blockchain that also protects user privacy.
The same Zero-knowledge proof can also be used to scale a network using ZK-Rollups. A ZK-Rollup helps the underlying network by moving some of the computation required to carry out a transaction off-chain and only sending the result of the computation back to the L1 chain. Validators on the L1 chain can use the Zero-Knowledge proof provided with the transaction to verify that the transaction has been executed correctly without going into the exact details of the transaction, which involves an encryption and decryption process. Such a method significantly decreases the processing time cost for each transaction. This in turn allows the L1 network to scale without having to compromise on decentralization or security.
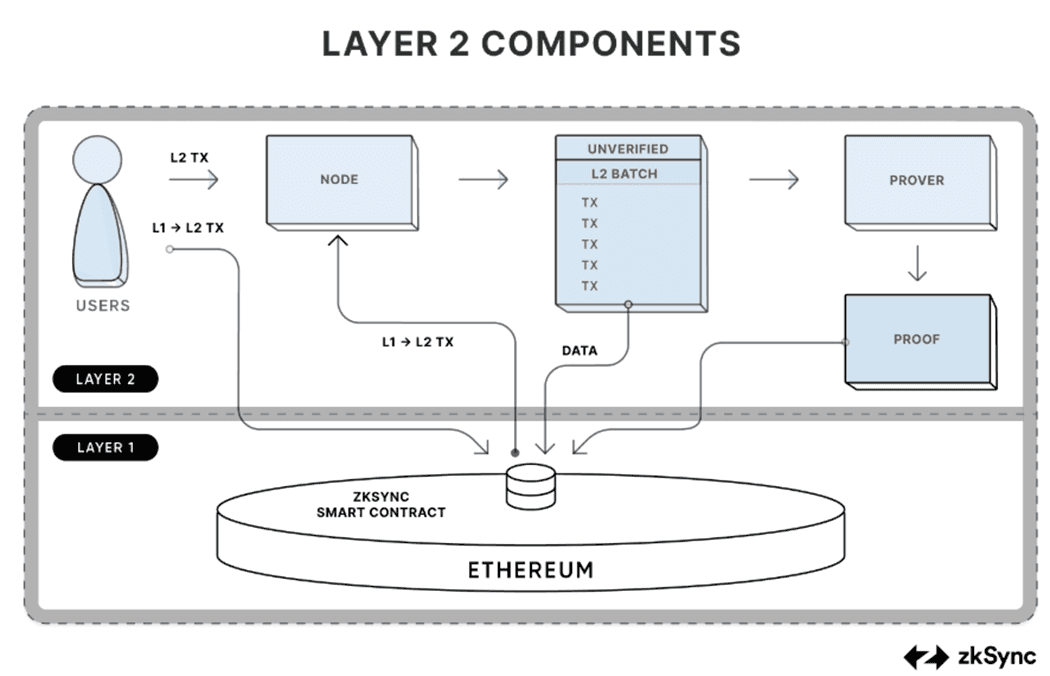
Layer-2 Transaction execution of ZK Sync Rollup
Cryptography plays a central role in the blockchain ecosystem. From initiating transactions to scaling the network, almost every part of the current blockchain ecosystem depends on the cryptographic principle. However, there is still room for more innovation in both cryptography and blockchain that could greatly benefit both the field. Let’s look at some of those below:
Earlier in the article, we covered how blockchain technology uses cryptographic algorithms, such as RSA and elliptic curve cryptography, which require miners to use a lot of computation resources to add blocks to the network. However, this process can be upended by the rise of quantum computing. Unlike classical computers, quantum computers might be able to solve these cryptographic algorithms with a fraction of the cost which would break the current model securing the blockchains. To combat this problem, the industry has been working on post-quantum cryptographic algorithms that aims to create puzzles that are resistant to quantum attacks.
With traditional encryption systems, data that are encrypted need to be decrypted to be computed. This requires additional computation resources as well as exposes the data to third-parties. Homomorphic encryption overcomes this problem by enabling computation to occur on encrypted data. This can allow user data to remain encrypted at all times on the blockchain, thereby greatly improving its privacy and security.
Advanced cryptographic algorithms are now being employed for improving blockchain consensus algorithms. Cryptographic techniques like Verifiable Random Functions and Cryptographic Sortition can be used to generate random sequence that ensures fairness and security, as long as just 2/3rd of the network participants are honest. Techniques like these are already getting implemented in chains like Algorand to improve the network’s speed without affecting its security.
Blockchains cannot exist without cryptography as it forms the basis of the entire technology. The use of cryptographic algorithms along with the access to the internet are the two pillars upon which a decentralized blockchain gets built. This approach has provided several benefits including
Using cryptographic algorithms, blockchains are able to create a digital ledger that's secured by mathematical codes. It's able to provide verifiable open ledger that can be used by anyone. The combination of public key and private key methods, along with output hash function allows legitimate users to transact with complete strangers and be confident that the transaction will get executed as it was intended.
The creation of blockchains has given rise to an entirely new era of the internet known as Web3. Cryptographic techniques and blockchain has enabled the rise of a censorship-resistant, decentralized internet that’s fully decentralized and doesn’t have any third-party intermediary, including decentralized data.

As blockchains become more successful, the need to scale them also increases. Cryptographic techniques like Zero-Knowledge Proofs can play a pivotal role in making sure the computational burden on the blockchain decreases by taking data offline while also making sure that the transaction is executed exactly as intended.
Cryptography is the unsung hero behind the success of blockchains and cryptocurrency. It forms the basis of what is currently a $3.5 trillion dollar industry and likely to be a $10 trillion industry in the future. Cryptography has also benefited from this development as new money and talent have flowed into this field and great strides have been made in improving techniques like Zero-Knowledge proof in the past years.
Blockchain technology has fundamentally transformed trustless transactions by creating an ecosystem where total strangers can transact with one another without the need for an intermediary. At the heart of this revolution lies cryptography, the science of encoding and decoding information. Blockchain networks use cryptography in several different ways to make sure only honest and legitimate transactions can go through the network and filter out any malicious activity.
Most people know about cryptocurrency and many own and use it. But only a few know about how cryptocurrencies work. In this article, let’s explore the role that cryptography plays in maintaining a blockchain and understand where the ‘crypto’ in cryptocurrency comes from.
Cryptography is the science of securing communication and information by encoding it on one end and decoding it on the other end. This process ensures that the communication can only be read by the intended recipient and no one else. In general, blockchain cryptography uses two different types of encryptions to encrypt data and achieve the process of encoding and decoding information.
Secret key cryptography, also known as symmetric key cryptography, is a process through which a single key is used to encrypt and decrypt the data on both ends. While simple to execute, this process creates a security risk, especially in large networks. Since the encryption and decryption keys are the same, anyone who manages to get the encryption key will also be able to decrypt the message, making it more susceptible to malicious attacks.
Also known as asymmetric key cryptography, this is a process through which a pair of related keys, one public and one private, is used to encrypt and decrypt the data. It can be used to convert plaintext into encrypted data using private keys to ensure the integrity and authenticity of the transaction data.
The public key of a network participant is available to everyone. Therefore, anyone can use it to encrypt a message to that particular person. This process is called ‘Public Key Encryption’ and it’s used to encrypt messages on an open network that can only be read by the intended recipient.
The private key is only available to the participant and therefore only they can use it to decrypt the message. The exact steps of asymmetric encryption are as follows:
The sender uses the receiver’s public key to encrypt the information.
Sender sends the encrypted information to the receiver.
Receiver uses the private key to carry out the decryption process and reveal the information.

All blockchains use cryptography extensively to secure their network. From making transactions to maintaining the integrity of the data on the blocks, cryptography forms the basis upon which most blockchain security. Let’s look at some of those use cases in detail:
The Asymmetric encryption method described above is used to make secure transactions on the blockchain. For example, on the Bitcoin network, when users send Bitcoin to others, they use the public key of the receiving user to encrypt that transaction. The transaction is then recorded on the blockchain and only the user who holds the private key can then decrypt that transaction and get access to the Bitcoin. This process secures the Bitcoins on the network, despite the network’s data being open to the public and the network itself being decentralized.
Cryptographic hashing is a mathematical function and a cryptographic algorithm that takes any input value and produces a fixed-size output known as a Hash. This function is used to create a cryptographic hash for each block in a blockchain that represents all the data within that particular block. If any miner or validator were to change the data stored on the blockchain ledger even slightly, the hash algorithm will produce a different hash value which will not match with the hash of other validators. This process makes it easy to detect malicious activity on the blockchain and secures data and networks integrity. It also makes sure the data on a blockchain is recorded securely, enhancing blockchain security.
Blockchain transactions are authenticated with digital signatures that are secured by cryptography. When a web3 user interacts with any smart contract and carries out a transaction, that transaction is authenticated by a private key, also known as secret key, that's stored in the wallet. This private key allows the blockchain network to verify that the person making the transaction is the owner of that account. It’s this process that also gives rise to the crypto maxim ‘Not your key, not your coin’. Because as far as the network is concerned, the person who owns the private key is the owner of the account.

Proof of Work blockchains like Bitcoin also rely on complex mathematical challenges based on cryptographic hash functions to validate new blocks. Miners compete to solve these puzzles and the first one to do so earns the right to add the next block to the blockchain. This process often requires significant computational resources which ensures that miners incur real costs to participate in the network. As a reward for their efforts, miners receive a specific amount of newly minted Bitcoin, this aligns the financial incentive of the miners with the security of the underlying blockchain ledger.
Adding cryptographic techniques like Zero-Knowledge proof can be used to protect user identity and transaction details. Zero Knowledge Proof allows one party to prove to another that a specific condition has been met without revealing any associated information. Such methods are used by privacy-focused blockchains like Zcash. It allows users to create transactions that does not reveal transaction data like the sender address, receiver’s address, and the amount of coins sent to the wider public. Using this method creates a fully public blockchain that also protects user privacy.
The same Zero-knowledge proof can also be used to scale a network using ZK-Rollups. A ZK-Rollup helps the underlying network by moving some of the computation required to carry out a transaction off-chain and only sending the result of the computation back to the L1 chain. Validators on the L1 chain can use the Zero-Knowledge proof provided with the transaction to verify that the transaction has been executed correctly without going into the exact details of the transaction, which involves an encryption and decryption process. Such a method significantly decreases the processing time cost for each transaction. This in turn allows the L1 network to scale without having to compromise on decentralization or security.

Layer-2 Transaction execution of ZK Sync Rollup
Cryptography plays a central role in the blockchain ecosystem. From initiating transactions to scaling the network, almost every part of the current blockchain ecosystem depends on the cryptographic principle. However, there is still room for more innovation in both cryptography and blockchain that could greatly benefit both the field. Let’s look at some of those below:
Earlier in the article, we covered how blockchain technology uses cryptographic algorithms, such as RSA and elliptic curve cryptography, which require miners to use a lot of computation resources to add blocks to the network. However, this process can be upended by the rise of quantum computing. Unlike classical computers, quantum computers might be able to solve these cryptographic algorithms with a fraction of the cost which would break the current model securing the blockchains. To combat this problem, the industry has been working on post-quantum cryptographic algorithms that aims to create puzzles that are resistant to quantum attacks.
With traditional encryption systems, data that are encrypted need to be decrypted to be computed. This requires additional computation resources as well as exposes the data to third-parties. Homomorphic encryption overcomes this problem by enabling computation to occur on encrypted data. This can allow user data to remain encrypted at all times on the blockchain, thereby greatly improving its privacy and security.
Advanced cryptographic algorithms are now being employed for improving blockchain consensus algorithms. Cryptographic techniques like Verifiable Random Functions and Cryptographic Sortition can be used to generate random sequence that ensures fairness and security, as long as just 2/3rd of the network participants are honest. Techniques like these are already getting implemented in chains like Algorand to improve the network’s speed without affecting its security.
Blockchains cannot exist without cryptography as it forms the basis of the entire technology. The use of cryptographic algorithms along with the access to the internet are the two pillars upon which a decentralized blockchain gets built. This approach has provided several benefits including
Using cryptographic algorithms, blockchains are able to create a digital ledger that's secured by mathematical codes. It's able to provide verifiable open ledger that can be used by anyone. The combination of public key and private key methods, along with output hash function allows legitimate users to transact with complete strangers and be confident that the transaction will get executed as it was intended.
The creation of blockchains has given rise to an entirely new era of the internet known as Web3. Cryptographic techniques and blockchain has enabled the rise of a censorship-resistant, decentralized internet that’s fully decentralized and doesn’t have any third-party intermediary, including decentralized data.

As blockchains become more successful, the need to scale them also increases. Cryptographic techniques like Zero-Knowledge Proofs can play a pivotal role in making sure the computational burden on the blockchain decreases by taking data offline while also making sure that the transaction is executed exactly as intended.
Cryptography is the unsung hero behind the success of blockchains and cryptocurrency. It forms the basis of what is currently a $3.5 trillion dollar industry and likely to be a $10 trillion industry in the future. Cryptography has also benefited from this development as new money and talent have flowed into this field and great strides have been made in improving techniques like Zero-Knowledge proof in the past years.
Blockchain technology has fundamentally transformed trustless transactions by creating an ecosystem where total strangers can transact with one another without the need for an intermediary. At the heart of this revolution lies cryptography, the science of encoding and decoding information. Blockchain networks use cryptography in several different ways to make sure only honest and legitimate transactions can go through the network and filter out any malicious activity.
Most people know about cryptocurrency and many own and use it. But only a few know about how cryptocurrencies work. In this article, let’s explore the role that cryptography plays in maintaining a blockchain and understand where the ‘crypto’ in cryptocurrency comes from.
Cryptography is the science of securing communication and information by encoding it on one end and decoding it on the other end. This process ensures that the communication can only be read by the intended recipient and no one else. In general, blockchain cryptography uses two different types of encryptions to encrypt data and achieve the process of encoding and decoding information.
Secret key cryptography, also known as symmetric key cryptography, is a process through which a single key is used to encrypt and decrypt the data on both ends. While simple to execute, this process creates a security risk, especially in large networks. Since the encryption and decryption keys are the same, anyone who manages to get the encryption key will also be able to decrypt the message, making it more susceptible to malicious attacks.
Also known as asymmetric key cryptography, this is a process through which a pair of related keys, one public and one private, is used to encrypt and decrypt the data. It can be used to convert plaintext into encrypted data using private keys to ensure the integrity and authenticity of the transaction data.
The public key of a network participant is available to everyone. Therefore, anyone can use it to encrypt a message to that particular person. This process is called ‘Public Key Encryption’ and it’s used to encrypt messages on an open network that can only be read by the intended recipient.
The private key is only available to the participant and therefore only they can use it to decrypt the message. The exact steps of asymmetric encryption are as follows:
The sender uses the receiver’s public key to encrypt the information.
Sender sends the encrypted information to the receiver.
Receiver uses the private key to carry out the decryption process and reveal the information.

All blockchains use cryptography extensively to secure their network. From making transactions to maintaining the integrity of the data on the blocks, cryptography forms the basis upon which most blockchain security. Let’s look at some of those use cases in detail:
The Asymmetric encryption method described above is used to make secure transactions on the blockchain. For example, on the Bitcoin network, when users send Bitcoin to others, they use the public key of the receiving user to encrypt that transaction. The transaction is then recorded on the blockchain and only the user who holds the private key can then decrypt that transaction and get access to the Bitcoin. This process secures the Bitcoins on the network, despite the network’s data being open to the public and the network itself being decentralized.
Cryptographic hashing is a mathematical function and a cryptographic algorithm that takes any input value and produces a fixed-size output known as a Hash. This function is used to create a cryptographic hash for each block in a blockchain that represents all the data within that particular block. If any miner or validator were to change the data stored on the blockchain ledger even slightly, the hash algorithm will produce a different hash value which will not match with the hash of other validators. This process makes it easy to detect malicious activity on the blockchain and secures data and networks integrity. It also makes sure the data on a blockchain is recorded securely, enhancing blockchain security.
Blockchain transactions are authenticated with digital signatures that are secured by cryptography. When a web3 user interacts with any smart contract and carries out a transaction, that transaction is authenticated by a private key, also known as secret key, that's stored in the wallet. This private key allows the blockchain network to verify that the person making the transaction is the owner of that account. It’s this process that also gives rise to the crypto maxim ‘Not your key, not your coin’. Because as far as the network is concerned, the person who owns the private key is the owner of the account.

Proof of Work blockchains like Bitcoin also rely on complex mathematical challenges based on cryptographic hash functions to validate new blocks. Miners compete to solve these puzzles and the first one to do so earns the right to add the next block to the blockchain. This process often requires significant computational resources which ensures that miners incur real costs to participate in the network. As a reward for their efforts, miners receive a specific amount of newly minted Bitcoin, this aligns the financial incentive of the miners with the security of the underlying blockchain ledger.
Adding cryptographic techniques like Zero-Knowledge proof can be used to protect user identity and transaction details. Zero Knowledge Proof allows one party to prove to another that a specific condition has been met without revealing any associated information. Such methods are used by privacy-focused blockchains like Zcash. It allows users to create transactions that does not reveal transaction data like the sender address, receiver’s address, and the amount of coins sent to the wider public. Using this method creates a fully public blockchain that also protects user privacy.
The same Zero-knowledge proof can also be used to scale a network using ZK-Rollups. A ZK-Rollup helps the underlying network by moving some of the computation required to carry out a transaction off-chain and only sending the result of the computation back to the L1 chain. Validators on the L1 chain can use the Zero-Knowledge proof provided with the transaction to verify that the transaction has been executed correctly without going into the exact details of the transaction, which involves an encryption and decryption process. Such a method significantly decreases the processing time cost for each transaction. This in turn allows the L1 network to scale without having to compromise on decentralization or security.

Layer-2 Transaction execution of ZK Sync Rollup
Cryptography plays a central role in the blockchain ecosystem. From initiating transactions to scaling the network, almost every part of the current blockchain ecosystem depends on the cryptographic principle. However, there is still room for more innovation in both cryptography and blockchain that could greatly benefit both the field. Let’s look at some of those below:
Earlier in the article, we covered how blockchain technology uses cryptographic algorithms, such as RSA and elliptic curve cryptography, which require miners to use a lot of computation resources to add blocks to the network. However, this process can be upended by the rise of quantum computing. Unlike classical computers, quantum computers might be able to solve these cryptographic algorithms with a fraction of the cost which would break the current model securing the blockchains. To combat this problem, the industry has been working on post-quantum cryptographic algorithms that aims to create puzzles that are resistant to quantum attacks.
With traditional encryption systems, data that are encrypted need to be decrypted to be computed. This requires additional computation resources as well as exposes the data to third-parties. Homomorphic encryption overcomes this problem by enabling computation to occur on encrypted data. This can allow user data to remain encrypted at all times on the blockchain, thereby greatly improving its privacy and security.
Advanced cryptographic algorithms are now being employed for improving blockchain consensus algorithms. Cryptographic techniques like Verifiable Random Functions and Cryptographic Sortition can be used to generate random sequence that ensures fairness and security, as long as just 2/3rd of the network participants are honest. Techniques like these are already getting implemented in chains like Algorand to improve the network’s speed without affecting its security.
Blockchains cannot exist without cryptography as it forms the basis of the entire technology. The use of cryptographic algorithms along with the access to the internet are the two pillars upon which a decentralized blockchain gets built. This approach has provided several benefits including
Using cryptographic algorithms, blockchains are able to create a digital ledger that's secured by mathematical codes. It's able to provide verifiable open ledger that can be used by anyone. The combination of public key and private key methods, along with output hash function allows legitimate users to transact with complete strangers and be confident that the transaction will get executed as it was intended.
The creation of blockchains has given rise to an entirely new era of the internet known as Web3. Cryptographic techniques and blockchain has enabled the rise of a censorship-resistant, decentralized internet that’s fully decentralized and doesn’t have any third-party intermediary, including decentralized data.

As blockchains become more successful, the need to scale them also increases. Cryptographic techniques like Zero-Knowledge Proofs can play a pivotal role in making sure the computational burden on the blockchain decreases by taking data offline while also making sure that the transaction is executed exactly as intended.
Cryptography is the unsung hero behind the success of blockchains and cryptocurrency. It forms the basis of what is currently a $3.5 trillion dollar industry and likely to be a $10 trillion industry in the future. Cryptography has also benefited from this development as new money and talent have flowed into this field and great strides have been made in improving techniques like Zero-Knowledge proof in the past years.
Share this article
Related Articles
Related Articles
Related Articles